Cyber Security: Public Networks & Wi-Fi Security
Cyber Security: Public Networks & Wi-Fi Security
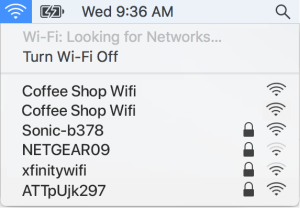
Some Key Statistics:
Airport Wi-Fi Networks, Paid In-Flight Services, and Hotel Wi-Fi's
How to protect yourself
The best way to protect yourself when using public Wi-Fi is by ensuring it’s a secured network with encryption technology. Make sure you use a strong password on your devices and consider using a virtual private network (VPN) that uses Full Tunneling, when you’re connected to public Wi-Fi.
A VPN using Full Tunneling encrypts all the data sent between your device and the router, making it harder for hackers to access your data. You should also avoid visiting sites that require you to enter personal information such as passwords or credit card numbers.
Note: This is referencing a personal VPN. Barracuda VPN uses split tunneling and will not protect you for general internet usage. It only creates a tunnel to the Method network resources.
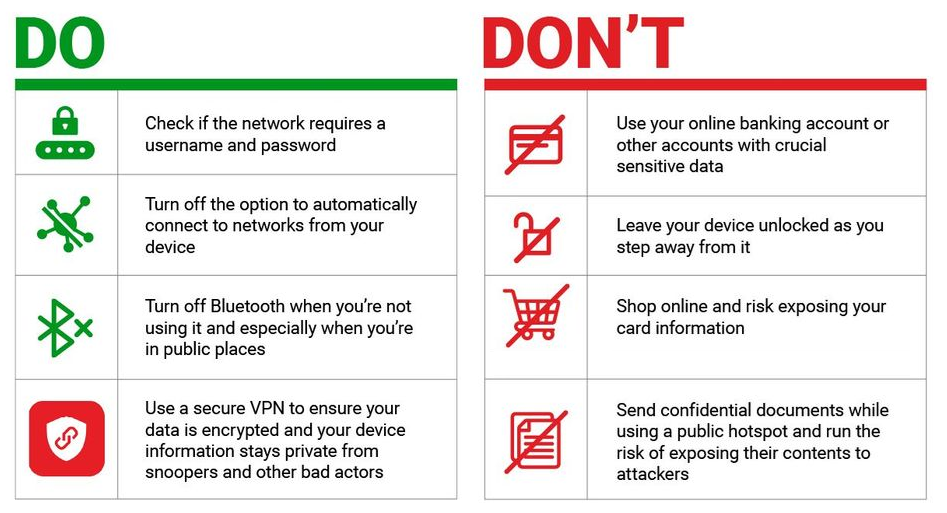
Cheat Sheet
How to Forget a Wi-Fi Network
If you don’t want your device to automatically rejoin a network, or you want it to join with a different password, you can make your device forget that network and its password.
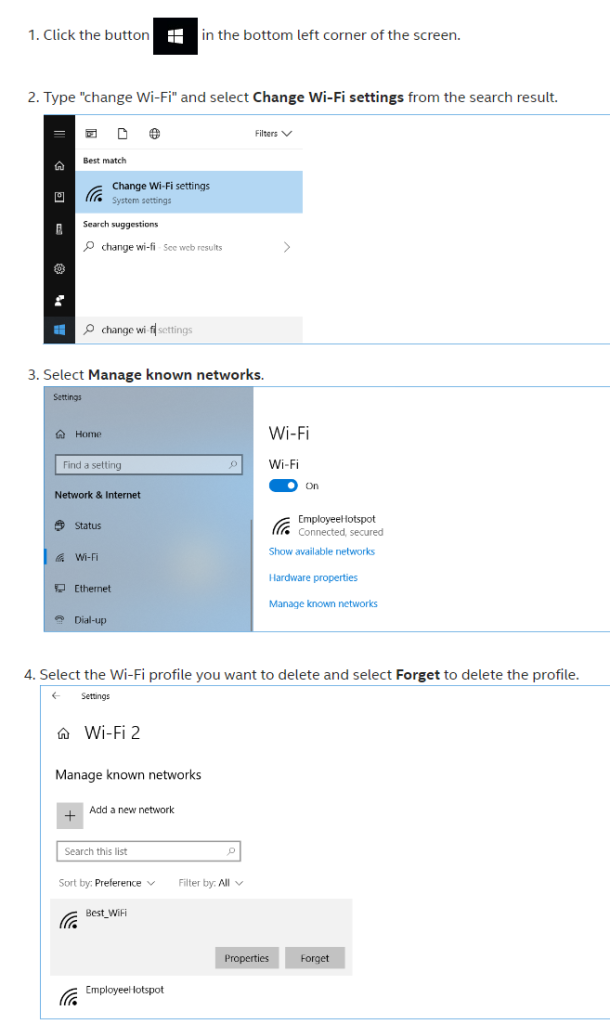
How to Forget a in Windows
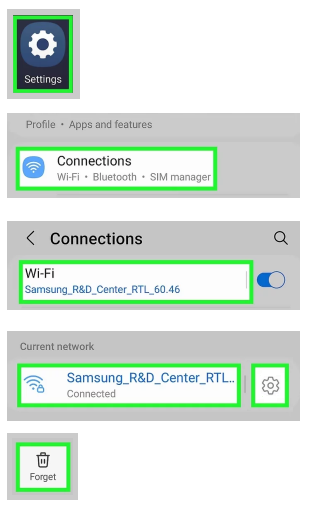
How to Forget on Android
- Open Settings.
- Tap Connections or Network & Internet.
- Tap Wi-Fi or Internet.
- Navigate to the Settings menu of the network you want to forget.
- Tap Forget.
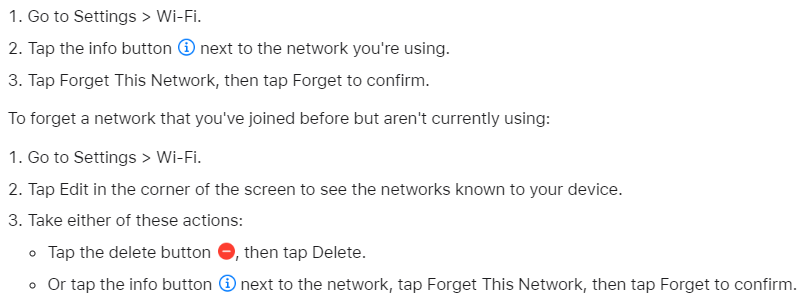
How to Forget on iPhone or iPad
Forget a network on iPhone or iPad
To forget the network that you’re currently using:
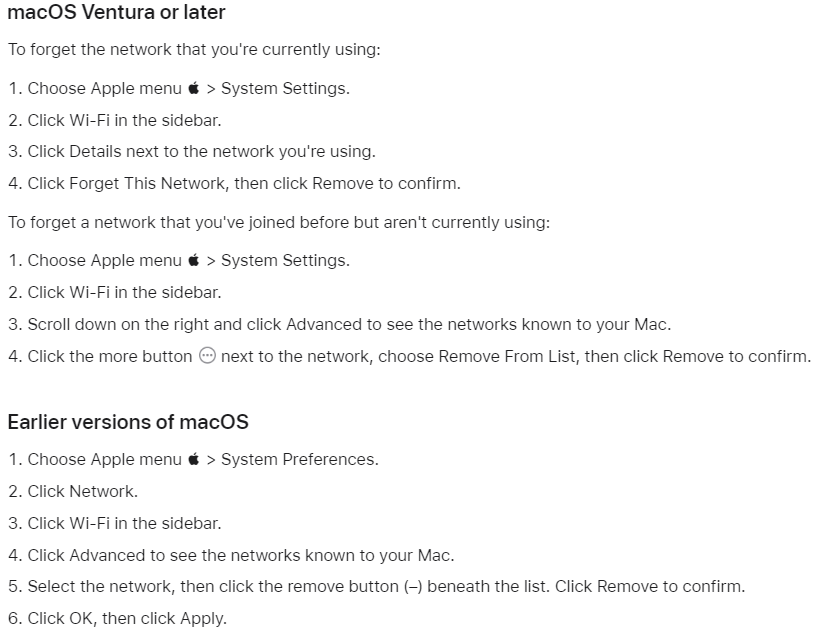
How to Forget a network on Mac
Is you Wi-Fi secure?
- Extremely slow Wi-Fi
- A surge in phishing emails or fake antivirus messages
- Unknown devices connecting to your router
- Unauthorized software installations
- An unexpected Wi-Fi password change
- Your router suddenly requiring a password
Common Wi-Fi Attacks
Password Attacks
Cracking attack (a form of Password Attack)
Man-in-the-Middle Attacks
Evil Twin Attack (a form of Man-in-the-Middle)
Rogue Access Points
Piggybacking (a form of Rogue Access Point Attack)
Eavesdropping aka Wireless Sniffing
Denial-of-Service Attacks
Related Articles
VPN: Troubleshooting Barracuda VPN Client
VPN: Troubleshooting Barracuda VPN Client Here are some troubleshooting steps to take if the VPN isn't connecting. Credentials: Your username should be your first initial last name. The password will be your computer password (not email). Your ...VPN: Understanding Virtual Private Networks (VPN)
VPN: Understanding Virtual Private Networks (VPN) VPN or Virtual Private Network - What is it? What does it do? Understanding Virtual Private Networks is key to safeguarding your information. VPN stands for Virtual Private Network. It's a service ...Cyber Security: Data Brokers – What Is Your Data Worth?
Cyber Security: Data Brokers – What Is Your Data Worth? A data broker (also known as an information product company) is an organization that makes money by collecting your personal information, analyzing it, and licensing it out to be used by other ...Cyber Security: Phishing Attacks
Cyber Security: Phishing Attacks What Is Phishing? Phishing is a fraud technique where a malicious actor sends messages impersonating a legitimate individual or organization, usually via email or other messaging system. Many cyber attackers ...Cyber Security: 5 things everyone should do to outsmart online criminals
Cyber Security: 5 things everyone should do to outsmart online criminals 1. Always be suspicious If you receive a video, phone call, voicemail, email, or direct message, try to confirm independently with the sender that it's real. If you don't ...